|
本文介绍在Ubuntu 20.04系统上安装和设置Wazuh Server的详细步骤,包含的内容有:安装依赖、从Open Distro安装Elasticsearch、安装证书、安装Filebeat、及安装Kibana。
步骤1:安装依赖 安装以下运行Wazuh Manager所需的软件包: sudo apt update sudo apt install curl apt-transport-https unzip wget libcap2-bin software-properties-common lsb-release gnupg2 然后再安装Java: sudo apt install default-jre
步骤2:在Ubuntu 20.04上安装Wazuh Server 以下步骤将指导我们如何在Ubuntu 20.04上安装Wazuh服务器。 1、添加GPG密钥 curl -s https://packages.wazuh.com/key/GPG-KEY-WAZUH | sudo apt-key add - 2、添加Wazuh存储库 echo "deb https://packages.wazuh.com/4.x/apt/ stable main" | sudo tee /etc/apt/sources.list.d/wazuh.list 3、更新系统 sudo apt update 4、安装Wazuh Manager sudo apt install wazuh-manager 5、启动并启用服务 sudo systemctl daemon-reload sudo systemctl enable --now wazuh-manager 检查Wazuh管理器的状态并确认它是否已启动并正在运行: systemctl status wazuh-manager 检查服务状态,是否是Active: active (running)。
步骤3:从Open Distro安装Elasticsearch 参考:在Ubuntu 20.04服务器上安装和配置Elasticsearch的方法。 Open Distro是高度可扩展的全文本搜索引擎,该软件包提供高级安全性、警报、深入的性能分析、索引管理和许多其他功能: sudo apt install elasticsearch-oss opendistro-alerting opendistro-anomaly-detection opendistro-index-management opendistro-job-scheduler opendistro-knn opendistro-knnlib opendistro-performance-analyzer opendistro-security opendistro-sql opendistroforelasticsearch 下载/etc/elasticsearch/elasticsearch.yml的定制配置文件,如下所示: sudo curl -so /etc/elasticsearch/elasticsearch.yml https://raw.githubusercontent.com/wazuh/wazuh-documentation/4.0/resources/open-distro/elasticsearch/7.x/elasticsearch_all_in_one.yml 使用以下模板配置Kibana角色和用户: sudo curl -so /usr/share/elasticsearch/plugins/opendistro_security/securityconfig/roles.yml https://raw.githubusercontent.com/wazuh/wazuh-documentation/4.0/resources/open-distro/elasticsearch/roles/roles.yml sudo curl -so /usr/share/elasticsearch/plugins/opendistro_security/securityconfig/roles_mapping.yml https://raw.githubusercontent.com/wazuh/wazuh-documentation/4.0/resources/open-distro/elasticsearch/roles/roles_mapping.yml sudo curl -so /usr/share/elasticsearch/plugins/opendistro_security/securityconfig/internal_users.yml https://raw.githubusercontent.com/wazuh/wazuh-documentation/4.0/resources/open-distro/elasticsearch/roles/internal_users.yml 上面的命令为Kibana添加了以下用户: Wazuh_user–将用于需要只读访问Wazuh Kibana插件的用户。 Wazuh_admin–适用于需要管理特权的用户。 还创建了两个其他角色,以为用户提供适当的权限。 wazuh_ui_user–提供wazuh_user权限以读取Wazuh的索引。 wazuh_ui_admin–允许wazuh_admins对wazuh索引执行读/写,管理和索引。
步骤4:安装证书 我们可以设置证书以用于Elasticsearch和Wazuh之间的TLS通信。 1、删除演示证书 sudo rm -f /etc/elasticsearch/{esnode-key.pem,esnode.pem,kirk-key.pem,kirk.pem,root-ca.pem} 2.生成新证书 sudo mkdir /etc/elasticsearch/certs && cd /etc/elasticsearch/certs sudo curl -so ~/search-guard-tlstool-1.8.zip https://maven.search-guard.com/search-guard-tlstool/1.8/search-guard-tlstool-1.8.zip 3、解压缩下载的文件 sudo unzip ~/search-guard-tlstool-1.8.zip -d ~/searchguard 4、下载预配置的search-guard.yml文件 sudo curl -so ~/searchguard/search-guard.yml https://raw.githubusercontent.com/wazuh/wazuh-documentation/4.0/resources/open-distro/searchguard/search-guard-aio.yml 5、运行搜索保护脚本以创建证书 sudo ~/searchguard/tools/sgtlstool.sh -c ~/searchguard/search-guard.yml -ca -crt -t /etc/elasticsearch/certs/ 6、创建证书后,删除不必要的文件 sudo rm /etc/elasticsearch/certs/client-certificates.readme sudo /etc/elasticsearch/certs/elasticsearch_elasticsearch_config_snippet.yml ~/search-guard-tlstool-1.8.zip ~/searchguard -rf 7、启用并启动Elasticsearch服务 sudo systemctl enable --now elasticsearch 8、通过运行Elasticsearch的securityadmin脚本来加载新证书 sudo /usr/share/elasticsearch/plugins/opendistro_security/tools/securityadmin.sh -cd /usr/share/elasticsearch/plugins/opendistro_security/securityconfig/ -nhnv -cacert /etc/elasticsearch/certs/root-ca.pem -cert /etc/elasticsearch/certs/admin.pem -key /etc/elasticsearch/certs/admin.key 您应该看到类似于以下内容的输出: WARNING: JAVA_HOME not set, will use /usr/bin/java Open Distro Security Admin v7 Will connect to localhost:9300 ... done Connected as CN=admin,OU=Docu,O=Wazuh,L=California,C=US Elasticsearch Version: 7.10.0 Open Distro Security Version: 1.12.0.0 Contacting elasticsearch cluster 'elasticsearch' and wait for YELLOW clusterstate ... Clustername: elasticsearch Clusterstate: GREEN Number of nodes: 1 Number of data nodes: 1 .opendistro_security index does not exists, attempt to create it ... done (0-all replicas) Populate config from /usr/share/elasticsearch/plugins/opendistro_security/securityconfig/ Will update '_doc/config' with /usr/share/elasticsearch/plugins/opendistro_security/securityconfig/config.yml SUCC: Configuration for 'config' created or updated Will update '_doc/roles' with /usr/share/elasticsearch/plugins/opendistro_security/securityconfig/roles.yml SUCC: Configuration for 'roles' created or updated Will update '_doc/rolesmapping' with /usr/share/elasticsearch/plugins/opendistro_security/securityconfig/roles_mapping.yml SUCC: Configuration for 'rolesmapping' created or updated Will update '_doc/internalusers' with /usr/share/elasticsearch/plugins/opendistro_security/securityconfig/internal_users.yml SUCC: Configuration for 'internalusers' created or updated Will update '_doc/actiongroups' with /usr/share/elasticsearch/plugins/opendistro_security/securityconfig/action_groups.yml SUCC: Configuration for 'actiongroups' created or updated Will update '_doc/tenants' with /usr/share/elasticsearch/plugins/opendistro_security/securityconfig/tenants.yml SUCC: Configuration for 'tenants' created or updated Will update '_doc/nodesdn' with /usr/share/elasticsearch/plugins/opendistro_security/securityconfig/nodes_dn.yml SUCC: Configuration for 'nodesdn' created or updated Will update '_doc/whitelist' with /usr/share/elasticsearch/plugins/opendistro_security/securityconfig/whitelist.yml SUCC: Configuration for 'whitelist' created or updated Will update '_doc/audit' with /usr/share/elasticsearch/plugins/opendistro_security/securityconfig/audit.yml SUCC: Configuration for 'audit' created or updated Done with success 运行以下命令以确认安装成功: curl -XGET https://localhost:9200 -u admin:admin -k 响应应如下所示: { "name" : "node-1", "cluster_name" : "elasticsearch", "cluster_uuid" : "9JuWWZBHSX65WNZioHQcMg", "version" : { "number" : "7.10.0", "build_flavor" : "oss", "build_type" : "deb", "build_hash" : "51e9d6f22758d0374a0f3f5c6e8f3a7997850f96", "build_date" : "2020-11-09T21:30:33.964949Z", "build_snapshot" : false, "lucene_version" : "8.7.0", "minimum_wire_compatibility_version" : "6.8.0", "minimum_index_compatibility_version" : "6.0.0-beta1" }, "tagline" : "You Know, for Search" } 您可能选择删除Open Distro for Elasticsearch性能分析器插件,该插件在默认情况下会安装,有时可能会占用大量资源。使用下面的命令将其删除: sudo /usr/share/elasticsearch/bin/elasticsearch-plugin remove opendistro_performance_analyzer
步骤5:在Ubuntu 20.04上安装Filebeat Filebeat用于将警报和事件从Wazuh服务器发送到Elasticsearch: sudo apt install filebeat 下载下面的filebeat配置文件,该文件将用于将wazuh警报转发到Elasticsearch: sudo curl -so /etc/filebeat/filebeat.yml https://raw.githubusercontent.com/wazuh/wazuh-documentation/4.0/resources/open-distro/filebeat/7.x/filebeat_all_in_one.yml 使用下面的命令为Elasticsearch下载警报模板: sudo curl -so /etc/filebeat/wazuh-template.json https://raw.githubusercontent.com/wazuh/wazuh/4.0/extensions/elasticsearch/7.x/wazuh-template.json sudo chmod go+r /etc/filebeat/wazuh-template.json 下载Wazuh FIlebeat模块: sudo curl -s https://packages.wazuh.com/4.x/filebeat/wazuh-filebeat-0.1.tar.gz | tar -xvz -C /usr/share/filebeat/module 将Elasticsearch证书复制到/etc/filebeat/certs: sudo mkdir /etc/filebeat/certs && cp /etc/elasticsearch/certs/root-ca.pem /etc/filebeat/certs/ sudo mv /etc/elasticsearch/certs/filebeat* /etc/filebeat/certs/ 启动并启用Filebeat服务: sudo systemctl enable --now filebeat 通过以下命令确认Filebeat配置: sudo filebeat test output 样本输出: elasticsearch: https://127.0.0.1:9200... parse url... OK connection... parse host... OK dns lookup... OK addresses: 127.0.0.1 dial up... OK TLS... security: server's certificate chain verification is enabled handshake... OK TLS version: TLSv1.3 dial up... OK talk to server... OK version: 7.10.0
步骤6:在Ubuntu 20.04上安装Kibana Kibana是一个Web界面,可帮助我们可视化和分析Elasticsearch中存储的事件。 使用以下命令在Ubuntu 20.04上安装Kibana: sudo apt-get install opendistroforelasticsearch-kibana 下载Kibana的配置文件: sudo curl -so /etc/kibana/kibana.yml https://raw.githubusercontent.com/wazuh/wazuh-documentation/4.0/resources/open-distro/kibana/7.x/kibana_all_in_one.yml 为以下文件分配正确的权限: sudo chown -R kibana:kibana /usr/share/kibana/optimize sudo chown -R kibana:kibana /usr/share/kibana/plugins 为Wazuh安装Kibana插件。这必须在Kibana主目录中完成: cd /usr/share/kibana sudo -u kibana /usr/share/kibana/bin/kibana-plugin install https://packages.wazuh.com/4.x/ui/kibana/wazuh_kibana-4.0.4_7.9.1-1.zip 将Elasticsearch证书复制到/etc/kibana/certs: sudo mkdir /etc/kibana/certs sudo cp /etc/elasticsearch/certs/root-ca.pem /etc/kibana/certs/ sudo mv /etc/elasticsearch/certs/kibana_http.key /etc/kibana/certs/kibana.key sudo mv /etc/elasticsearch/certs/kibana_http.pem /etc/kibana/certs/kibana.pem 将Kibana的套接字绑定到特权443端口: sudo setcap 'cap_net_bind_service=+ep' /usr/share/kibana/node/bin/node 启动并启用Kibana服务: sudo systemctl enable --now kibana 允许Kibana通过防火墙: sudo ufw allow 443/tcp 您现在可以通过访问wazuh kibana界面,有用的信息如下: URL: https://<wazuh_server_ip> user: admin password: admin
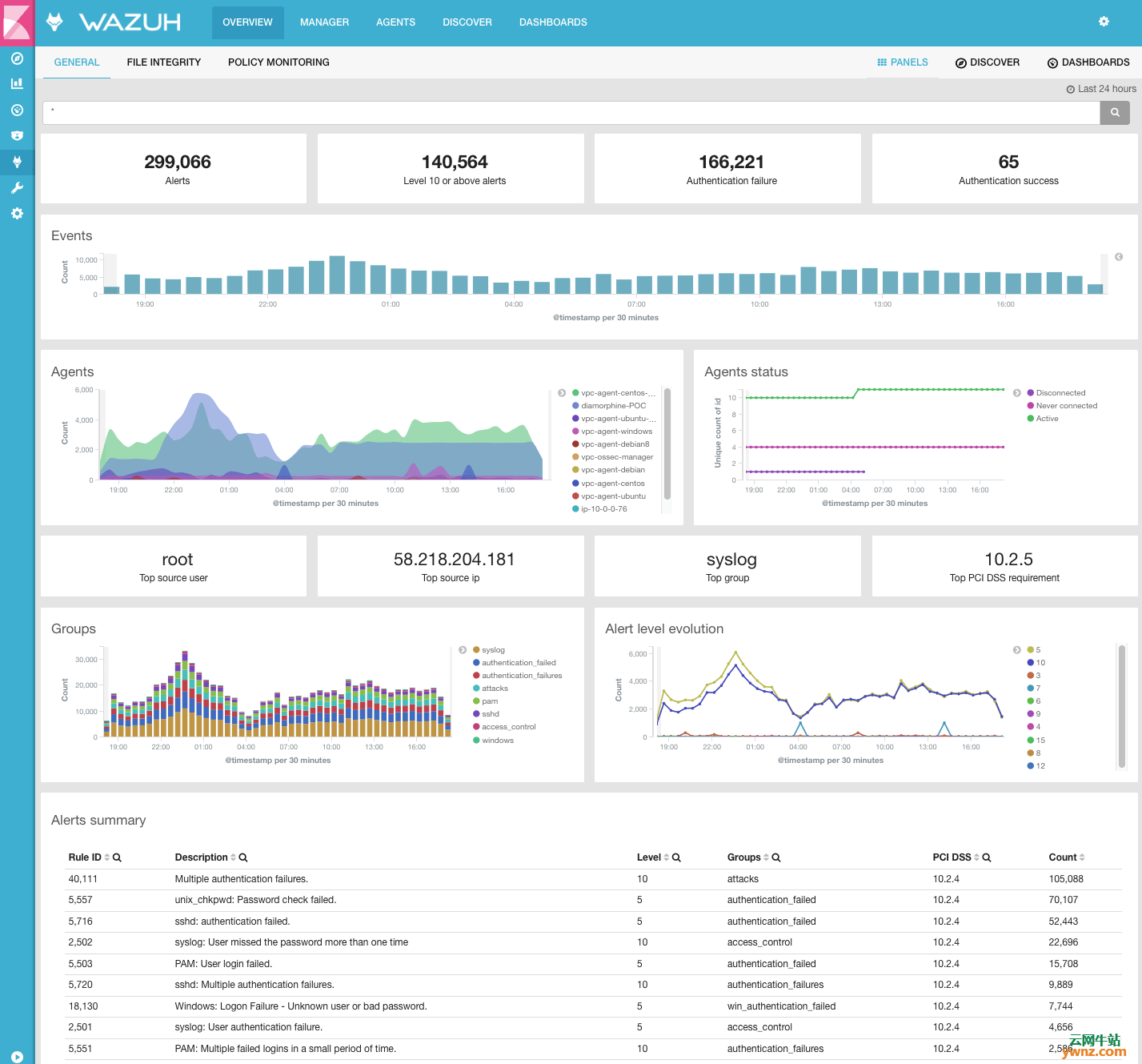
您可以登录并继续查看来自Wazuh的可用指标:
至此,通过以上步骤,我们已经在Ubuntu 20.04上成功设置了Wazuh服务器。
相关主题 |